During the renowned
A Closer Look at Windows Vulnerabilities
The Win-DoS Epidemic encapsulates four major DoS vulnerabilities, characterized by uncontrolled resource consumption, each with significant implications. These include a high-severity DoS in Windows LDAP, Network Logon (Netlogon), and LSASS, all carrying a CVSS score of 7.5, along with a medium-severity DoS vulnerability in the Windows Print Spooler. The latter requires an authenticated attacker from an adjacent network to exploit effectively.
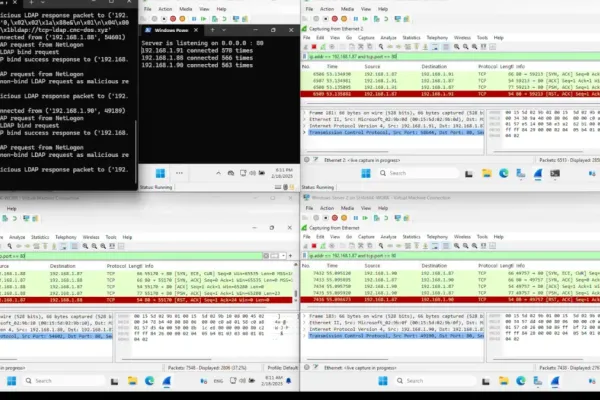
These vulnerabilities allow attackers to target and crash any Windows endpoint or server, notably critical Domain Controllers. This vulnerability not only compromises the functionality of these systems but also opens avenues for more complex attack strategies.
Win-DoS epidemic: a new DoS threat to Windows systems
Exploiting Domain Controllers for DDoS
One of the more unsettling discoveries from the researchers is the potential for leveraging Domain Controllers in expansive DDoS attacks, referred to as Win-DDoS. This technique uses the Windows LDAP client referral process to incite a destructive attack. By skillfully manipulating DC referrals, attackers can orchestrate a scenario where a vast number of public DCs are tricked into directing traffic to a single victim, forming an overwhelming DDoS botnet.
The exploitation of RPC bindings further underlines the sophistication of these findings. By bypassing concurrency limits, the researchers identified multiple unauthenticated DoS vulnerabilities, casting a shadow over Windows systems. These vulnerabilities expose critical systems to unauthorized attacks that can severely disrupt operations.
Implications and Next Steps
These revelations by SafeBreach Labs researchers build on past explorations, like CVE-2024-49113, also known as LdapNightmare, which emphasized the glaring risks DoS attacks pose to Domain Controllers. As the keystone of authentication and resource accessibility, DCs are vital, yet vulnerable targets.
In response, Microsoft has initiated the rollout of crucial patches to remedy some of these vulnerabilities. However, this research underscores the necessity for organizations to continuously evaluate and strengthen threat models. Key components, including LDAP, LSASS, Netlogon, RPC, and Print Spooler, should be scrutinized. Patching should not only be prompt but should also be part of a broader strategy involving routine security validation.