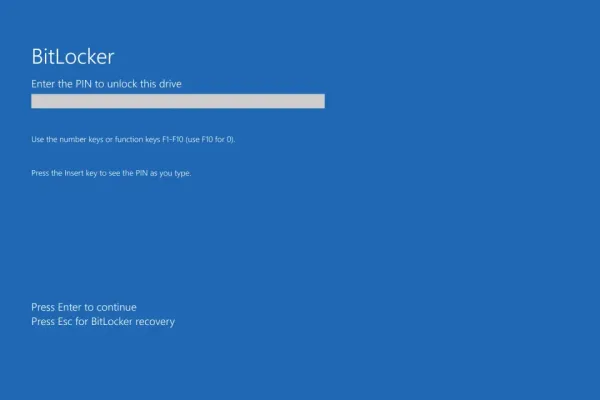
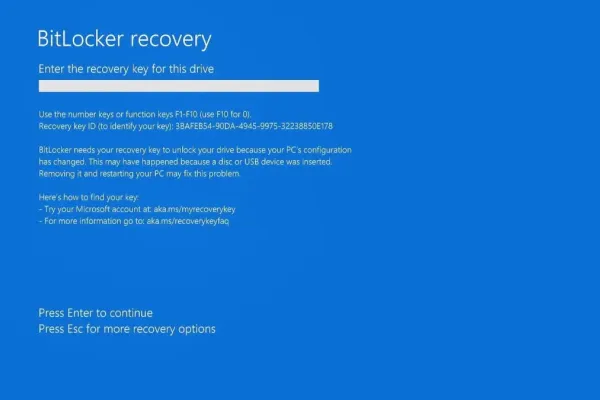
Microsoft's BitLocker encryption can offer substantial data protection, yet recent revelations show that its security guarantees may not be as robust as presumed. Microsoft confirmed that BitLocker recovery keys, essential for decrypting encrypted data, might be handed to law enforcement if a valid legal order is presented, particularly when these keys are backed up to Microsoft's cloud services.
FBI Access to BitLocker Keys
In a recent case in Guam involving a COVID-19 unemployment fraud investigation, the FBI required access to BitLocker-protected devices. Microsoft provided the necessary recovery keys, citing their cloud storage as the determining factor. This incident underscores the complexity of balancing convenience with security.
Security experts highlight a crucial trade-off: BitLocker secures data on lost or stolen devices, but cloud-backed keys are vulnerable to legal demands. The situation underscores the need for users to carefully consider where they store recovery keys and the accompanying risks.
Management Strategies for BitLocker
Microsoft advises users on managing BitLocker settings effectively. In Windows 11 and 10, navigate to Settings > System > About > Related settings > BitLocker. Users are advised to generate and secure recovery keys locally rather than in the cloud, minimizing potential access by third parties.
- Store recovery keys securely on a USB drive or as a printed document in a secure location.
- If the key is stored in the cloud, download it locally and delete the cloud copy.
- Consider additional security by encrypting keys or using password managers.
This guidance aligns with best practices for achieving a balance between accessibility and security, highlighting the importance of maintaining control over private encryption keys.