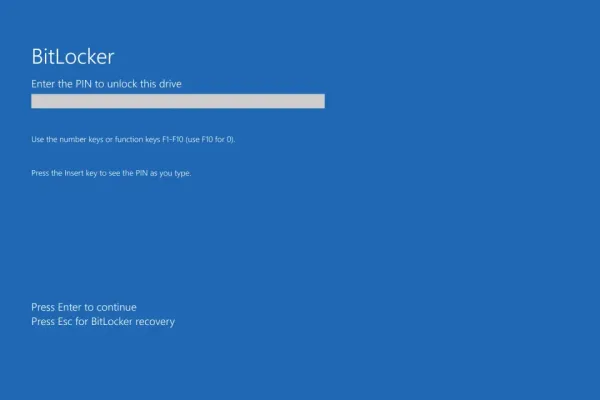
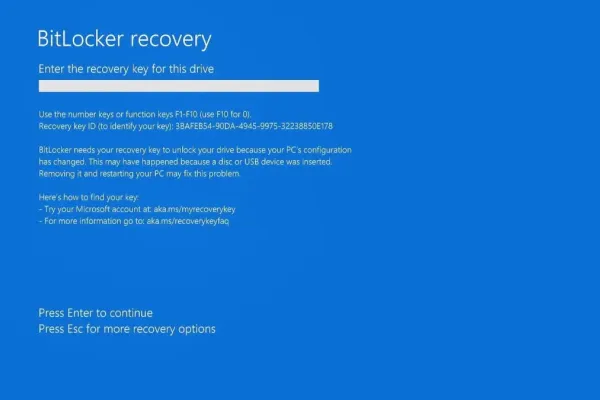
How to Crack a Single Hash with a Powerful Password Recovery Tool
Cracking a hash—a seemingly random string of characters that represent data like passwords—can be a daunting task, but with the right techniques, it can become manageable. This guide will walk you through the necessary steps to crack a single hash utilizing a robust password recovery tool, renowned for its speed and versatility.Understanding Hashing
Before diving into the cracking process, it’s essential to understand what hashing is. Hashing is a one-way mathematical process that converts data into a fixed-length string of characters. Examples of hashing algorithms include MD5, SHA-1, and SHA-256. Each hash type has its own characteristics and vulnerabilities, making some easier to crack than others.Required Tools and Preparation
To crack a hash successfully, you’ll need the following:- A powerful password recovery tool known for its efficiency.
- A file containing the hashes you want to crack.
- A wordlist—this might include common passwords or phrases that users typically select.
Steps to Crack a Single Hash
Follow these steps to crack an individual hash:- Identify the Hash Type: Knowing whether it’s MD5, SHA-1, etc., allows you to tailor your attack. Tools often provide identification features.
- Prepare Your Wordlist: Create or download a comprehensive wordlist. Ensure it contains common passwords, phrases, and variations.
- Run the Tool: Using the command line or software GUI, input your hash and the wordlist path. For example, a basic command might look like this:
hashcat -m 0 -a 0 your_hash.txt your_wordlist.txt.
Utilizing Cracking Options
Most password recovery tools offer various cracking modes. Depending on your needs, you might choose: - Dictionary Attack: Efficient with proper wordlists. - Brute Force Attack: Tries every possible combination, but time-consuming. - Rule-Based Attack: Combines dictionary attacks with changes (like leetspeak). Cracking might not always succeed, especially with stronger hashes. It’s important to select the right strategy based on the selected hashing algorithm and your password list authoring.Post-Cracking Steps
Once you successfully crack a hash, consider these actions:- Secure Your Findings: Store cracked results securely.
- Assess Security: If it’s a test scenario, analyze password strength.
- Document Your Process: Note the steps and tricks that yielded success for future reference.