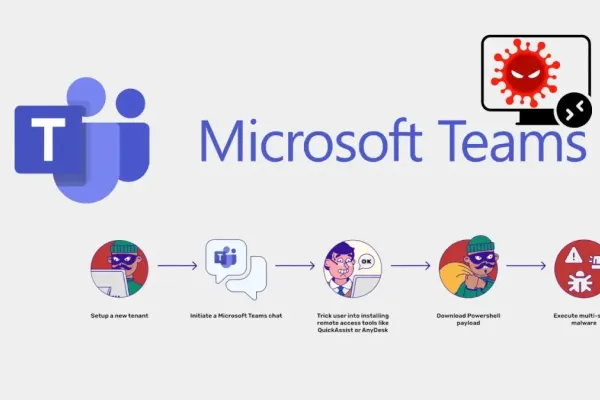
Cybercriminals are abusing sponsored ads mimicking Microsoft Teams downloads to distribute Rhysida ransomware, prompting concerns among security experts. The fraudulent ads divert users to cloned websites, where they unknowingly download malware disguised as legitimate applications.
Campaign Tactics and Impact
This campaign uses a combination of malvertising and SEO poisoning to promote these harmful downloads. The malicious software, including Rhysida's OysterLoader, is often signed with fraudulent certificates, helping it evade initial antivirus detection. Once installed, the malware can encrypt files, steal credentials, and create backdoors within the victims' systems.
According to Microsoft, over 200 illegitimate certificates were revoked in October 2025 to mitigate these threats. The tech giant has continually warned users of the dangers associated with downloading software from unverified sources.
Security Risks and Countermeasures
The attacks highlight the hazards of using search engines for downloading software, as criminals frequently exploit search algorithms to spread malware. The rise of remote work has increased the attempt to weaponize platforms like Microsoft Teams for unauthorized data access and deceptive activities.
Security specialists recommend several measures to counter these threats: downloading software directly from the official vendor’s website, implementing advanced endpoint protection, continuously monitoring certificate usage, and cultivating user awareness regarding suspicious ads and downloads. Further insights and strategies are available in Microsoft's security bulletins for comprehensive digital defense.