Cybercriminals are increasingly targeting Microsoft Teams, leveraging the platform's integral role in business communication to execute sophisticated cyberattacks. This shift from traditional email-based phishing techniques to using Teams is proving to be a significant challenge for organizations striving to maintain secure digital environments.
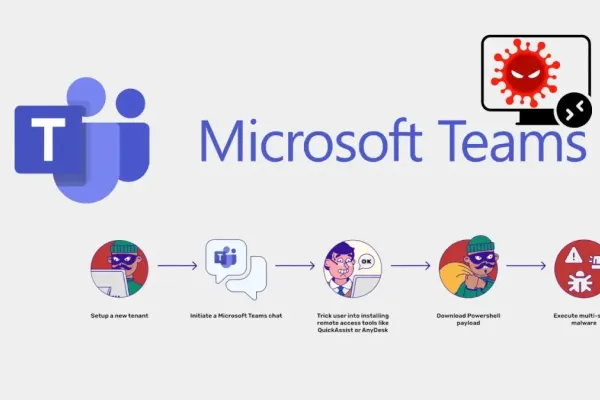
In a particularly insidious strategy, hackers utilize Teams to impersonate IT support personnel. By adopting convincing display names such as "IT SUPPORT ✅" or "Help Desk Specialist," these threat actors exploit the inherent trust placed in internal communication platforms. Initiating contact through either newly created or compromised Teams accounts, they masquerade as support staff using onmicrosoft.com domain addresses to enhance their credibility.
Deceptive Tactics and Exploited Trust
The attack typically begins with a direct message or call. By posing as IT staff, the attackers gradually build rapport with employees, persuading them to install remote access software like QuickAssist or AnyDesk. Once granted remote access, the true danger unfolds as a PowerShell command is executed to deliver a primary malicious payload.
This payload often consists of notorious loaders such as DarkGate and Matanbuchus. A PowerShell-based script enables the execution of remote code, credential theft, persistence establishment, and, disturbingly, critical process designation. This designation can crash the system if tampered with, complicating mitigation efforts. Capturing passwords through legitimate-seeming Windows prompts, attackers exfiltrate this sensitive information to their own servers.
Further analysis has uncovered hardcoded encryption keys within the malware, linking these activities to a financially motivated group tracked as Water Gamayun. These developments heighten the urgency for robust cybersecurity protocols in corporate environments.
Defensive Strategies and Awareness
To counter these threats, businesses are urged to adopt comprehensive defense measures. Employee training is paramount, emphasizing the importance of verifying unsolicited internal contacts. Any requests for credentials or remote-access installations should be independently confirmed via established, trustworthy channels.
Moreover, a defense-in-depth strategy should be adopted, combining technical security controls with user education to enhance resilience against such digital intrusions.
Indicators of compromise related to these attacks have been published to help organizations identify and thwart potential breaches. These include specific URLs, IP addresses, user agents, encryption keys, and user principal names that have been associated with recent campaigns.