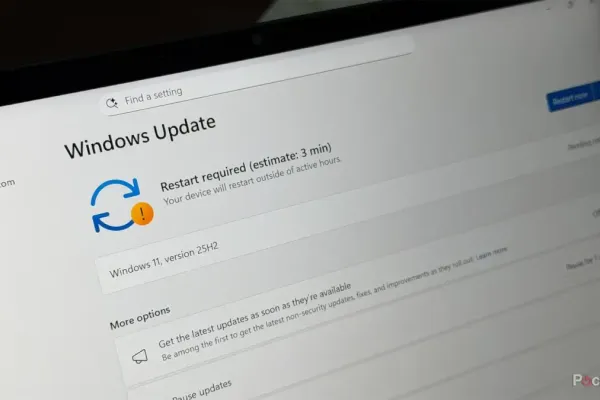
A fake Windows Update screen is currently being exploited to distribute malware, affecting multiple platforms worldwide.
Fake Updates and Malware
Cybercriminals have engineered a realistic-looking Windows Update screen to trick users into installing malware. This method employs multi-stage delivery chains to infiltrate systems. Key platforms, including JSONFormatter and CodeBeautify, are reportedly exposing sensitive data like credentials and keys, exacerbating security concerns.
Enterprise Security Breaches
Salesforce has issued warnings and indicators of compromise following a breach of Gainsight-published applications, first noted on 2025-11-08. This incident underscores the vulnerability of widely used software and the persistent threat of reconnaissance activities.
AI technologies are also at risk: Cato Networks has identified a prompt-injection technique capable of making AI browsers disseminate phishing links and disinformation or disclose data inadvertently.
Emerging Vulnerabilities and Solutions
Amidst these threats, security teams are addressing phishing tactics through calendar invites. To combat this, Microsoft has updated Defender for Office 365 to enhance malicious domain blocking and remove residual malicious calendar entries.
Tor developers are enhancing their security protocols with an upcoming encryption upgrade, Counter Galois Onion (CGO). Meanwhile, practical security measures such as robust authentication protocols and password managers remain recommended defenses.
The cybersecurity landscape continues to evolve, with threats often originating from stolen credentials, phishing attacks, and unpatched systems. Ongoing vigilance and adaptation to new security tools are crucial in mitigating these risks.