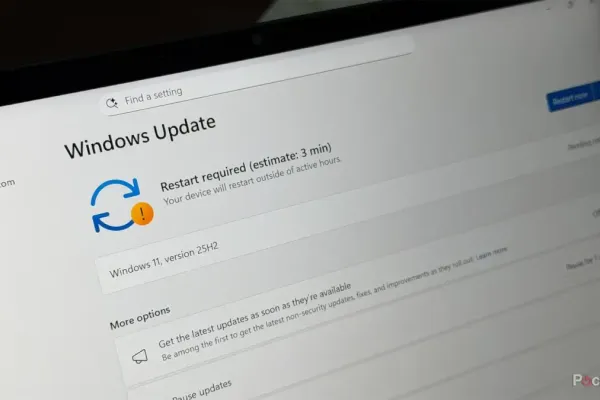
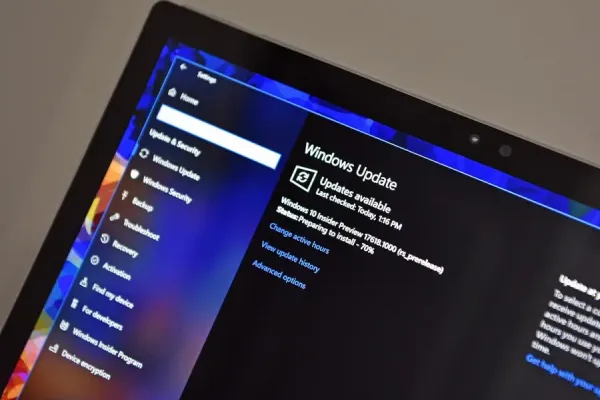
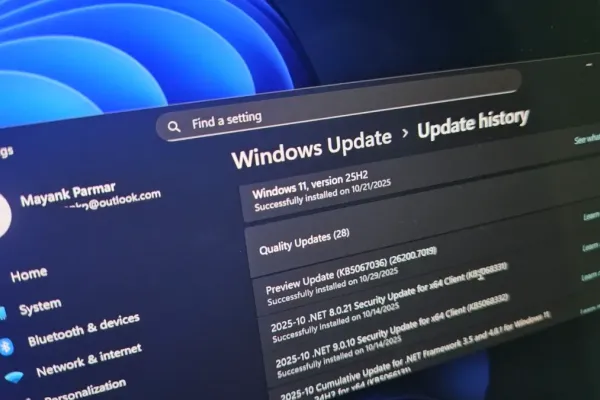
At the Black Hat security conference in Las Vegas, new research has unveiled a significant vulnerability within the Windows Update mechanism that could potentially allow malicious actors to downgrade Windows operating systems to older versions. This downgrade could expose systems to a range of historical vulnerabilities, ultimately granting attackers full control over the affected devices. Microsoft is currently addressing this issue through a meticulous patching process, which has been dubbed “Downdate.”
Discovery and Implications
Alon Leviev, a researcher from SafeBreach Labs, initiated his investigation into downgrade attack methods after observing a concerning hacking campaign last year that employed the “BlackLotus UEFI bootkit.” This malware exploited a vulnerability by downgrading the Windows boot manager to an outdated version. Through his exploration of the Windows Update flow, Leviev identified a method to strategically downgrade either the entire operating system or select components.
Leviev's findings led to the development of a proof-of-concept attack that effectively disabled the Windows protection known as Virtualization-Based Security (VBS), targeting highly privileged code within the computer's core kernel. “I found a downgrade exploit that is fully undetectable because it is performed by using Windows Update itself,” Leviev explained. “In terms of invisibility, I didn’t uninstall any update—I basically updated the system even though under the hood it was downgraded. So the system is not aware of the downgrade and still appears up-to-date.”
Mechanics of the Vulnerability
The crux of Leviev's downgrade capability lies in a flaw within the Windows Update process components. When a user requests an update, their PC places this request in a designated update folder, which is then verified by the Microsoft update server. The server creates a separate, controlled update folder where it finalizes the update and maintains an action list, known as “pending.xml,” detailing the update steps.
Leviev discovered that while he could not directly modify the action list in the server's folder, one of the controlling keys, “PoqexecCmdline,” was not secured. This oversight allowed him to manipulate the action list and the entire update process without detection. With this newfound control, he devised strategies to downgrade critical Windows components, including:
- Drivers that interact with hardware peripherals
- Dynamic link libraries containing essential system programs and data
- The NT kernel, which holds the core instructions necessary for system operation
Moreover, Leviev expanded his research to include Windows security components such as the Windows Secure Kernel, Credential Guard, the hypervisor, and VBS itself. While the technique does not provide a means to gain initial remote access, it poses a severe risk for attackers who already have some level of access, as it can reinstate numerous vulnerabilities that Microsoft has previously patched.
Microsoft's Response
In response to these findings, Microsoft has stated that it has not yet observed any attempts to exploit this vulnerability. A spokesperson emphasized, “We are actively developing mitigations to protect against these risks while following an extensive process involving a thorough investigation, update development across all affected versions, and compatibility testing, to ensure maximized customer protection with minimized operational disruption.”
Part of the remediation strategy includes revoking vulnerable VBS system files, a process that must be executed with caution to avoid integration issues or the reintroduction of previously resolved problems.
Leviev underscores the importance of recognizing downgrade attacks as a significant threat for the developer community, as hackers continuously seek stealthy avenues to exploit system vulnerabilities.