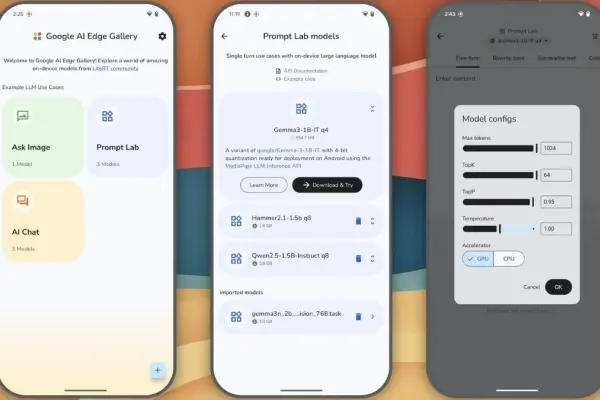
Google is gearing up for a major revelation at its next I/O conference, aiming to redefine the landscape of mobile AI development. Developers can look forward to the introduction of Gemini Nano, a new suite of advanced on-device AI tools designed to revolutionize how applications interact with users.
Introducing Gemini Nano
At the core of this initiative is Gemini Nano, an innovative move by Google to provide robust AI capabilities on mobile devices. While the tech giant has long been a player in the AI field, Gemini represents a significant advancement in on-device processing power. By enabling generative AI tasks such as text summarization and image description directly on the device, Google is taking strides to maintain data privacy, alleviating the need to constantly send data to the cloud.
Gemini's advanced AI tools for mobile developers
ML Kit SDK Enhancements
Central to this new offering is the enhancement of the ML Kit SDK with new APIs specifically designed for Gemini's functionalities. These APIs will allow developers to integrate powerful AI features into their applications seamlessly, enriching user experiences by leveraging local device capabilities. For the developer community, this is an exciting opportunity to enhance mobile applications with cutting-edge AI without compromising on privacy.
Beyond the Pixel
While Google’s own Pixel devices will certainly benefit from Gemini’s capabilities, the initiative is set to extend its reach beyond just Google's hardware. Android devices of various brands stand to gain; however, the extent of Gemini's functionality may vary depending on each device's hardware specifications. This variance underscores both the potential of Gemini and the current challenges facing diversified mobile platforms.
Privacy-Centric Approach
In an era where data privacy is paramount, Google’s commitment to performing AI tasks on-device aligns with growing demands for safeguarding user information. By minimizing dependency on cloud processing, Gemini not only enhances computational efficiency but also fortifies trust by ensuring sensitive data remains within the user's control.
The application of